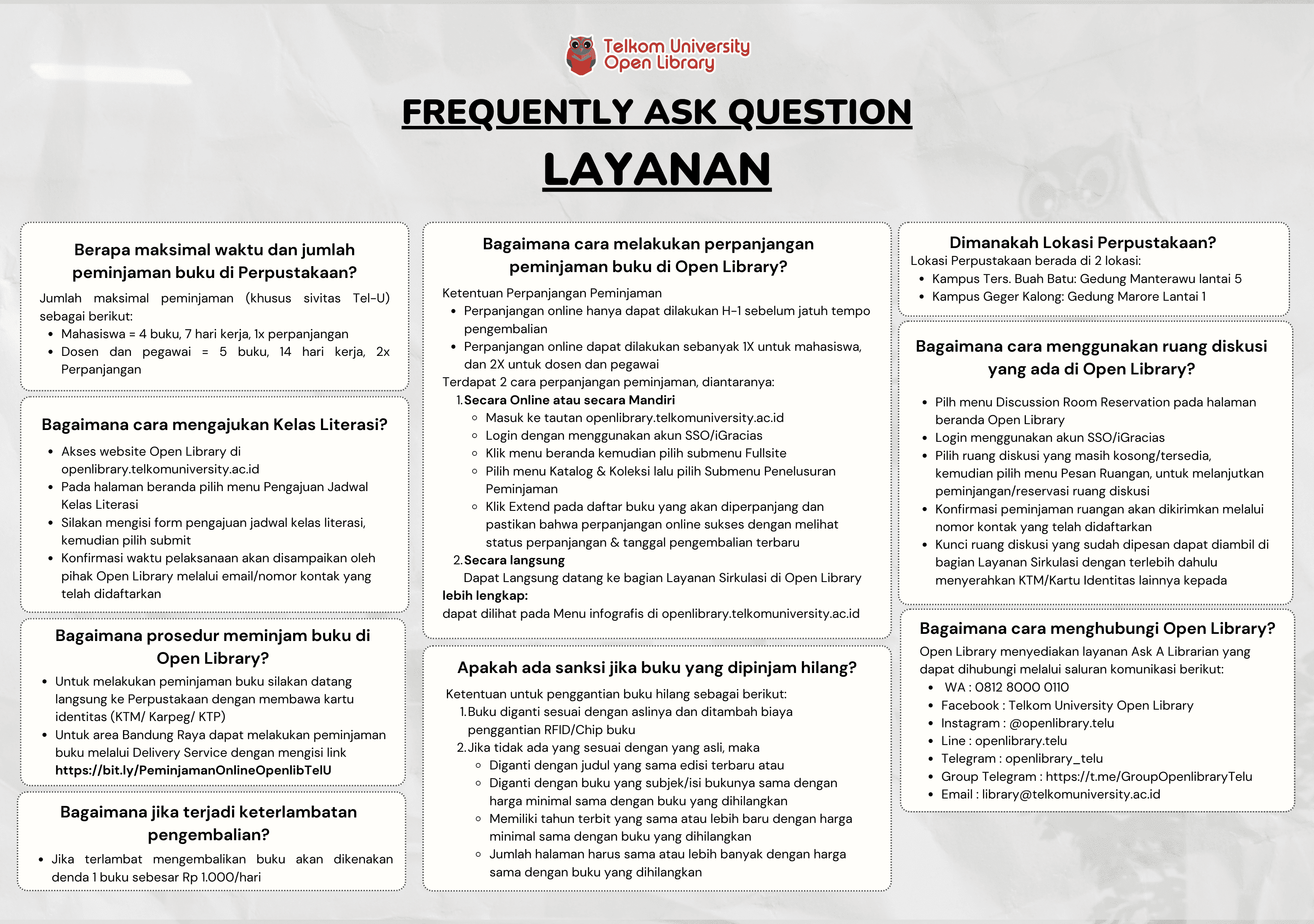
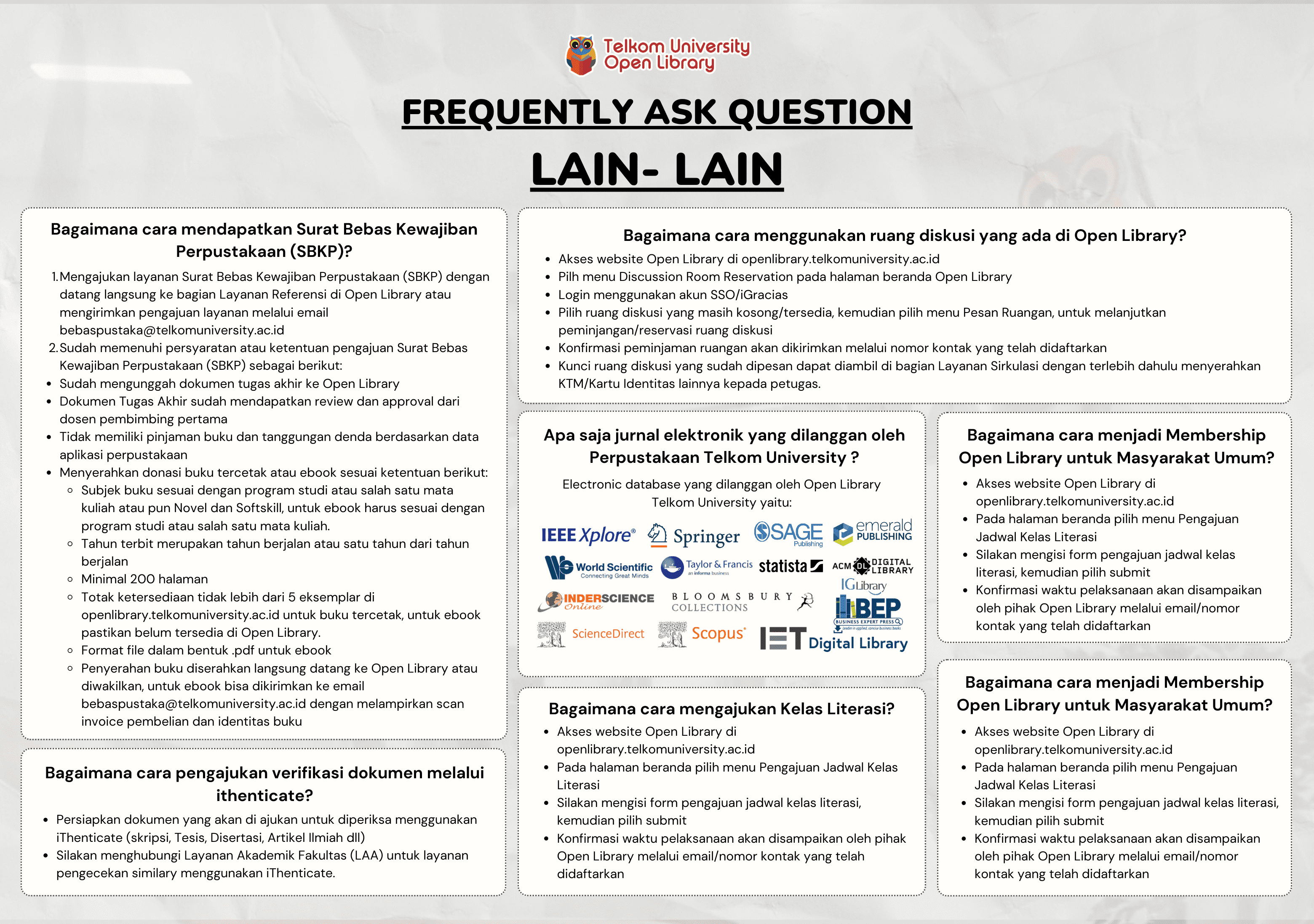
Intel-Based Macintosh Memory Forensics: Eavesdropping Attack Analysis Through Memory Dump - Dalam bentuk buku karya ilmiah
FARHAN MUHAMMAD ALIF

Informasi Umum
Kode
25.04.386
Klasifikasi
000 - General Works
Jenis
Karya Ilmiah - Skripsi (S1) - Reference
Subjek
Digital Forensics
Dilihat
289 kali
Informasi Lainnya
Abstraksi
<p>Memory forensics plays a critical role in cybersecurity, particularly in analyzing volatile memory during cyberattacks. This paper examines memory forensics analysis on Intel-based Macintosh systems targeted by remote attacks within shared networks. The study used a controlled setup involving an Intel-based Macintosh running a vulnerable PHP-based web application, DVWA (Damn Vulnerable Web Application). The system was attacked via SQL injection, command injection, and reflected Cross-Site Scripting (XSS) from a Kali Linux device over shared Wi-Fi. The attacks exploited application vulnerabilities to compromise the system, necessitating forensic examination. Memory dumps from the Mac device were analyzed using tools like the Volatility Framework to extract artifacts such as process details, network activity, and injected code. Memory artifacts were correlated with Wireshark packet analysis to uncover network-level evidence. The findings underscored the impact of remote attacks on system integrity and the ef
- CCH4D4 - TUGAS AKHIR
- CII4E4 - TUGAS AKHIR
Koleksi & Sirkulasi
Tersedia 1 dari total 1 Koleksi
Anda harus log in untuk mengakses flippingbook
Pengarang
| Nama | FARHAN MUHAMMAD ALIF |
| Jenis | Perorangan |
| Penyunting | Niken Dwi Wahyu Cahyani, Vera Suryani |
| Penerjemah |
Penerbit
| Nama | Universitas Telkom, S1 Informatika |
| Kota | Bandung |
| Tahun | 2025 |
Sirkulasi
| Harga sewa | IDR 0,00 |
| Denda harian | IDR 0,00 |
| Jenis | Non-Sirkulasi |